In the first part of our series, A Guide to Protecting and Monitoring Your Personal Cyber Security, we review the latest thinking and guidelines around using two-factor authentication (2FA) and passwords to protect your online identity.
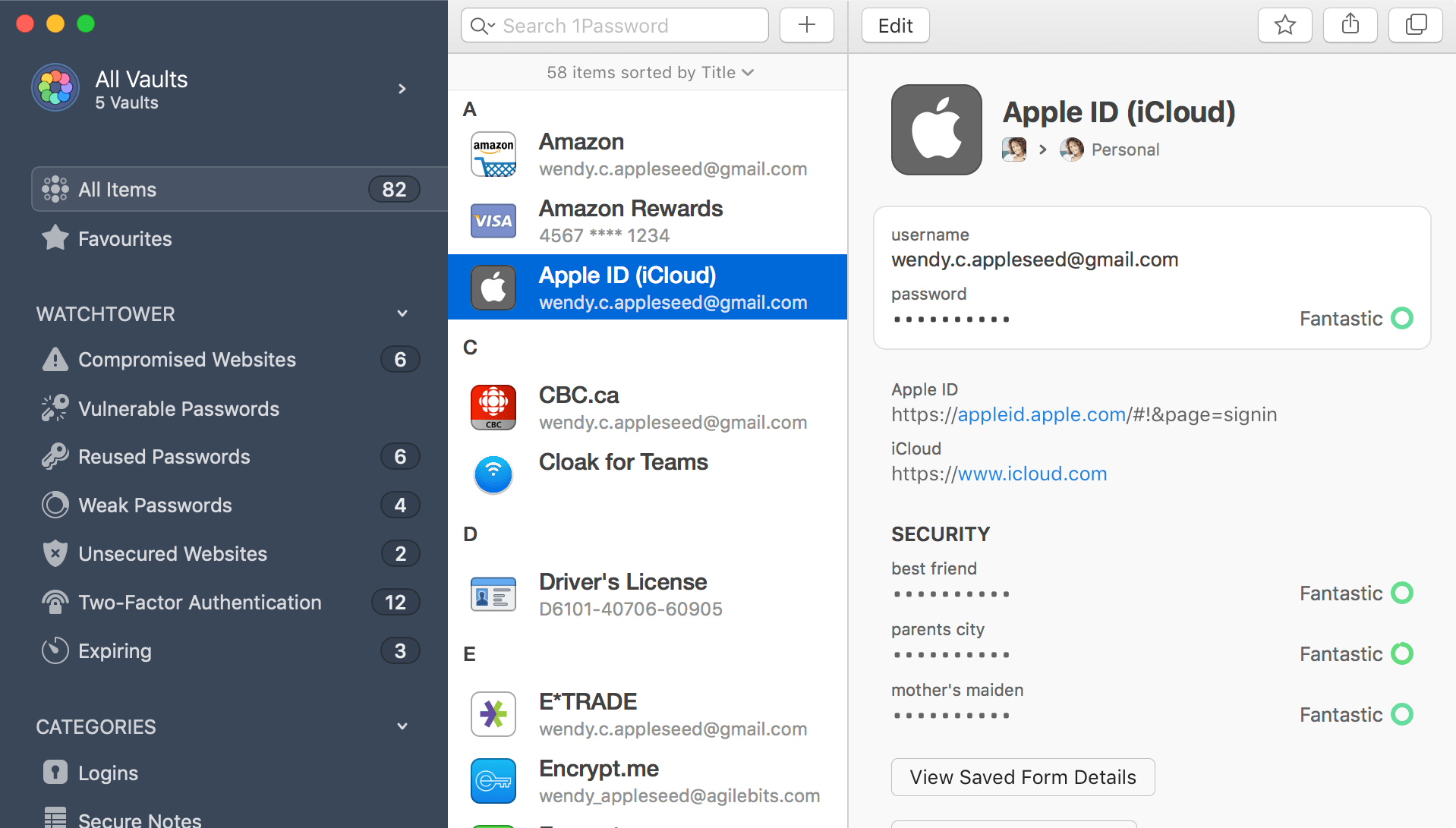
2FA adds an extra layer of security and should be enabled for your 1Password account. You should enable both an authenticator app and security key as a backup (which you should store with your recovery kit discussed in 2.1). 1.10 Enable 2 factor authentication. 1Password Family recover with 2FA If I recover an account that has 2FA enabled, during the recovery phase (choice of new master password, generation of a new secret key, etc) is 2FA disabled or will the recovered user have to enter his old 2FA? I made this video to show how to enable 2fa on your GitLab account using 1Password.It also highlights a bug with the 1Password browser extension that prevent. Two-factor authentication provides an extra layer of protection for your 1Password account. If you have a U2F-compatible security key, you can use it as a se.
Criminals want your identity credentials so they can steal from you or mask their identity when committing a crime. With the increasing scale and sophistication of attacks today, using just a password to access a service or website is not a good idea. Coupling 2FA with a password manager is a much better way to ensure identity safety.
What Is 2FA?
Two-factor authentication (2FA) is a method of identity confirmation that relies on a combination of two different factors. Examples of factors include 1) something you know, 2) something you have, or 3) something you are. Some examples of 2FA: using a debit card in combination with a PIN, or combining a password with a code sent to your phone.
2FA is one type of multi-factor authentication (MFA). MFA can have two or more factors and, it stands to reason, if you are using all three factors from the list above, you have better online security. An example of MFA would be using a debit card, a PIN, and a retina scan.
Security Questions: A Bad MFA Method
Security questions are not a good example of multi-factor authentication. Yes, the answer counts as a second piece of data (it’s something that you know) but, increasingly, it’s something that is very easy to discover. The ‘sharing economy’ means your favorite color, the name of your high school, or your favorite sports team isn’t exactly secret any longer.
In addition, the sheer number of data breaches means that harvesting data from a social network may not even be necessary. A breach trends research report by F5 Labs concludes that “there have been so many breaches that attacker databases are enriched to the point where they can impersonate an individual and answer secret questions to get direct access to accounts without ever having to work through the impacted party.”
The report found that 3,360,563,907 secret question and answer records were compromised in the 338 analyzed cases that included breach counts.
Which 2FA Method Should I Use?
So, given that security questions aren’t a good approach, how should you implement 2FA? There are basically three widely-implemented 2FA methods: hardware token, app, and SMS text message.
Today, pairing something you know (like a password) with a hardware token (something you have) offers the most security. At login, you insert the hardware token and it emits a one-time password or generates a secure public/private key pair to give you access. YubiKey is one such token that works with Google, Facebook, Windows, Dropbox, and many more services.
Authenticator apps such as Authy, Google Authenticator, and Microsoft Authenticator are dedicated apps typically installed on your phone. You then use your name and password combination, and the app provides an additional one-time password. As with hardware tokens, these options typically work with a huge selection of popular services.
The least-secure 2FA method today is one that pairs your login credentials with a code sent via SMS as the second factor. This method is much less secure than the other two because text messages can be hijacked.
Where – and How – Do I Use 2FA?
Once you’ve researched the various hardware token and authenticator app vendors and selected a few finalists, visit the vendor websites to see the list of services their product supports. This will likely help you narrow down your list of finalists.
Once you’ve selected your vendor, chances are that the vendor’s website will provide detailed tutorials on enabling 2FA using their product and your favorite service. Alternately, Turn It On provides many tutorials as well.
Finally, if your favorite service isn’t yet 2FA-ready, twofactorauth.org provides a robust list of services and the types of 2FA each supports. They even make it easy to reach out via Twitter or Facebook to services that don’t support 2FA so you can urge them to support 2FA.
Passwords and Password Managers
In a recent post, we talked about the latest thinking on how to create strong passwords. The important highlights:
- The length of the password is important.
- Regularly changing passwords or creating complex passwords is not recommended.
Also not recommended: documenting your password on a sticky note attached to your monitor.
However, you can do away with much of the worry about passwords simply by investing in a password manager. Password managers do the work of generating and storing strong passwords for the sites you use – across mobile devices and desktop systems. These apps use advanced encryption to keep your information safe.
PC Magazine, Lifehacker, and The Wire Cutter have recent reviews and ratings on password managers.
Combining 2FA and a Password Manager
To strengthen your online protection, pair 2FA with a password manager. By using 2FA to log into your password manager, you get additional security to protect your password list. So, for example, you would use your authenticator app to log into your password manager, and then use the authenticator app again to complete the login to your online service.
Recent articles have cautioned against using 2FA built into the password manager itself. In one case, an implementation flaw was identified. Another article warns of putting many eggs into one basket. Instead, considering implementing both a 2FA method and a password manager.
There’s no such as perfect security. But using 2FA and a password manager will go a long way to protecting your online identity. Click below to learn more about Teramind.
Protect And Monitor Your
Organization’s Data With Teramind
1password Authenticator
Tip
If you don’t have a U2F security key, use two-factor authentication with an authenticator app.
Set up your security key
Before you can use your security key as a second factor for your 1Password account, you’ll need to turn on two-factor authentication for your 1Password account. Then follow these steps:
- Sign in to your account on 1Password.com on your computer.
- Click your name in the top right and choose My Profile.
- Click More Actions > Manage Two-Factor Authentication.
- Click Add a Security Key.
If you don’t see Add a Security Key, turn on two-factor authentication for your 1Password account.
- Enter a name for your security key and click Next.
- Insert your security key into the USB port on your computer.
If Windows Security asks you to create a PIN, enter one and click OK. Your PIN is stored locally on your security key.
- Touch the sensor on your security key.
- When you see “Your security key was successfully registered”, click Done.
From now on, you can use your security key instead of a six-digit authentication code to sign in to your 1Password account in your browser, 1Password for iOS, and 1Password for Android.
View and manage your security keys
To view your security keys:
- Sign in to your account on 1Password.com.
- Click your name in the top right and choose My Profile.
- Click More Actions > Manage Two-Factor Authentication.
To prevent a security key from being used as a second factor, click Remove next to it.
To allow another security key to be used as a second factor, click Add a Security Key and follow the onscreen instructions.
Learn how to view and manage computers and mobile devices that are authorized to use your 1Password account.
Get help
You can use your security key as a second factor for your 1Password account:
- on 1Password.com
- on your iPhone or iPad (requires YubiKey 5 NFC, YubiKey 5C NFC, or YubiKey 5Ci)
- on your Android device
Using your security key as a second factor requires:
- a 1Password membership with two-factor authentication turned on
- a U2F security key, like YubiKey or Titan
To sign in to your account in the 1Password apps or in a browser without U2F support, enter a six-digit authentication code from your authenticator app.
If you lose access to your security key
If you lose access to your security key, you can still sign in to your 1Password account:
On 1Password.com
When you’re asked for your security key, click Cancel. Then click “Use your authenticator app instead” and enter a six-digit authentication code from your authenticator app.
On your iPhone or iPad
1password For Windows
When you see Two-Factor Authentication Required, choose Authentication Code, then enter a six-digit authentication code from your authenticator app.
On your Android device
When you see “Use your security key with 1Password”, tap the back button on your device and enter a six-digit authentication code from your authenticator app.
2fa With 1password Free
Get help if you also lost access to your authenticator app.
